
IS CYBERSECURITY INSURANCE REALLY NECESSARY?
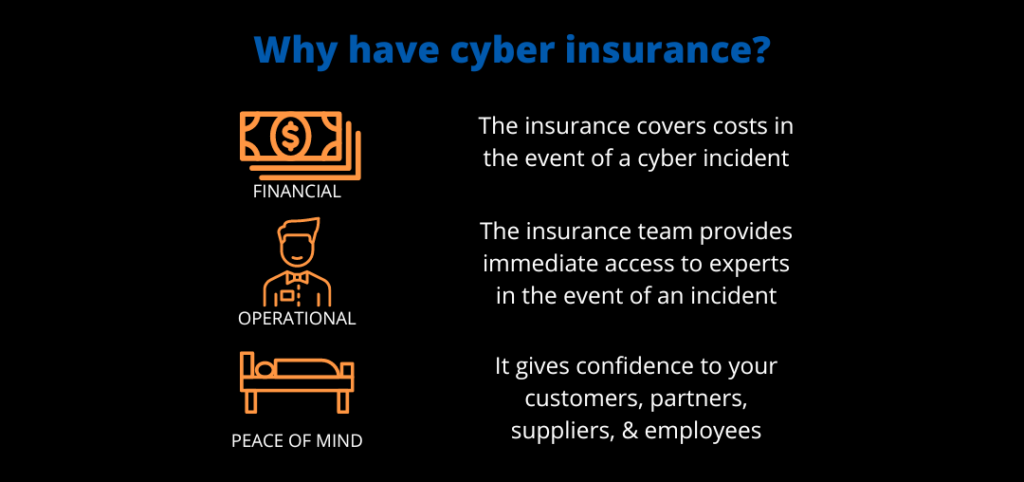
Cyber insurance is essential in helping your company recover after an attack or incident.
Cyber attacks have been steadily increasing worldwide and all businesses that use the internet to conduct their business are at risk. The cost of business disruption, revenue loss, equipment damages, legal fees, public relations expenses, forensic analysis and legally mandated notifications, cyber security insurance is more important now than ever.
As attacks continue to rise, cyber insurance is becoming increasingly difficult to secure. Strengthening your defenses reduces your risk of making a claim following a major cyber incident, while incident response planning and testing reduces the cost and impact of an attack. Cyber insurance providers require organizations to deploy strong cybersecurity controls as a condition of providing coverage.
The top 5 cybersecurity controls that are commonly
considered key to insurability, mitigation, and resilience by cyber insurance providers are:
- Multifactor Authentication (MFA / 2 Step) for remote access and admin/privileged controls
- Endpoint Detection and Response (EDR)
- Secured, encrypted, and tested Backups
- Privileged Access Management (PAM)
- Email filtering and web security
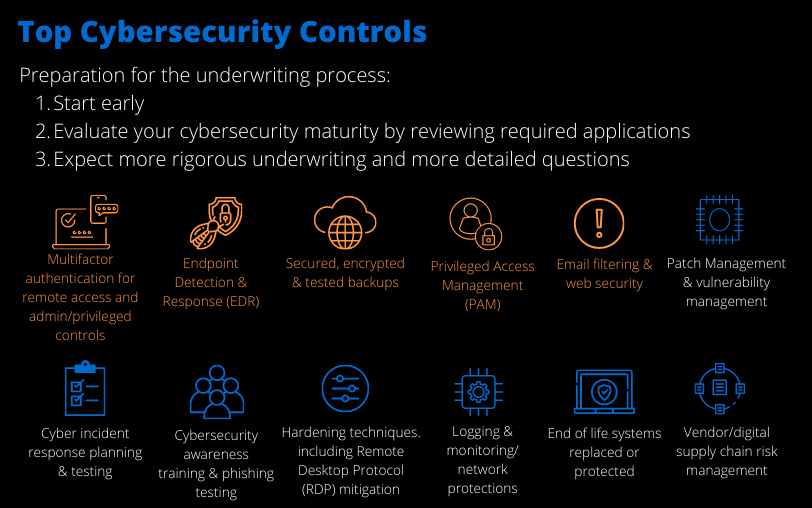
Without a positive response in these categories, your business may not be able to secure coverage.
Cybersecurity Compliance Services can help
Having good IT hygiene, policies and procedures that follow best practices, and keeping your company in compliance for your industry are some of the most important factors to mitigate your risks and successfully apply for a cyber security insurance policy.
EXAMPLES OF THE TYPES OF QUESTIONS YOUR INSURANCE PROVIDER WILL WANT TO KNOW
Who is Managing your infrastructure & what is being managed?
- Do you have a Chief Privacy Officer, or Chief Information Officer who has responsibility for meeting worldwide obligations under privacy and data protection laws?
- Do you have a written information security plan and privacy policy which outlines the company policy and procedures for the secure care, handling, storage and access of private, sensitive or confidential information?
- Do these policies and procedures comply with laws governing the handling and/or disclosure of such information?
- What is the company policy and procedures for the secure care, handling, storage and access of private, sensitive or confidential information?
How are the policies and or procedures measured?
- Do you perform security audits to ensure compliance with the security policy?
- Who performs the audits?
- Frequency of audits?
- Are security recommendations always followed?
- Do you perform privacy audits to ensure compliance with their privacy policy?
- Who performs the audits?
- Frequency of audits?
- Are security recommendations always followed?
Are your employees aware of the policies and trained?
Are all employees trained for your security privacy policies, do you have documentation of training?
What information are you collecting as part of your business?
- Do you employ electronic information gathering techniques (spyware, adware, cookies etc.)?
- Do you collect, process or maintain personal information as part of business activities including collecting over a website?
- Does your website display a privacy disclosure statement?
- What type of private and sensitive information do you receive, store, use or process:
- financial account payment information
- credit card or debit account number
- chequing, banking or automated clearing house information
- financial data
- Government issued identification information
- Name, address, contact information
- Medical or health related information
- Information on children who use your website
- are there controls in place to obtain parental permission
- trade secrets or intellectual property information
- third party corporate information
- Provide the number of records maintained by the company containing the information noted above
- What percentage of the above live in the United States?
- Any personal or private information gathered from customers or users, sold, disclosed or distributed to any third party?
- If yes, is prior permission obtained from the customers or clients?
- Is employee access to personally identifiable or sensitive information:
- on a business need to know basis?
- terminated immediately when an employee exits the company?
- Are third party vendors provided private or sensitive information?
- If yes, is there a review completed of the third party vendor’s information security plan?
Security Measures
- Describe security of the business’s premises and facilities
- Describe security measures used to prevent access to your systems or servers (both internally and externally)
- Describe security measures used to protect confidentiality and integrity of your company’s data or data which is entrusted to you
- Describe the technology used by the company for the following:
- Encryption
- Authentication
- Anti-Virus
- Firewall
PCI DSS Compliant
- If you accepts credit or payment card transactions for the payment of goods or services, are you compliant with applicable data transaction compliance standards (i.e. Payment Card Industry Data Security Standard compliance)?
Security Controls
- Do you have access control procedures and hard drive encryption to prevent unauthorized exposure of data on all laptops, PDAs, smartphones (e.g. BlackBerry) and home-based personal computers?
- Do you encrypt all sensitive and confidential information:
- That is physically removed from the premises by tape, disk hard drive or other means?
- That is stored in your databases, servers or individual files?
- That is transmitted within and from your organization?
- Do you ensure that all wireless networks have protected access?
- Do you have a document and e-mail retention and destruction policy?
- Do you enforce a software update process, including patches and anti-virus software?
- How frequently are computer systems and data backups performed?
- Are backups stored off-site in a secure location?
Breaches and Prevention
- Describe all security breaches and privacy complaints or violations that have occurred in the last 5 years
- Describe preventive measures taken to avoid future security breaches or privacy violations:
Third Party Vendors and / or Services
- Are any of the following network system functions outsourced to a third party?
- Hosting Facility
- Co-location Facility
- Management Security Services Provided
- Data Storage Facility
- Other (provide details):
- If yes:
- Is a written agreement in place with the third party provider?
- Does the agreement require a level of security commensurate with the company’s information systems security policy?
Previous Insurers
- Provide details of all Cyber Liability Insurance held during the past three years
- When was the first date on which the Applicant purchased continuous claims made coverage?
- Has any insurance been refused or canceled in the past five years?
- Does the company or any other person proposed for this insurance have knowledge or information of any claim, demand, suit, or proceeding which has been made or is pending against any insured proposed for coverage under the proposed insurance?
- Have there been any suits, claims, occurrences (including allegations) made against the company or any other person proposed for this insurance in the last five years?
- Has the company been subject to any government action, investigation or subpoena regarding any alleged violation of a privacy law or regulation in the last five years?
- Has the company notified consumers or any other third party of a data breach incident involving the applicant in the last five years?
- Has the company experienced an actual or attempted extortion demand with respect to its computer systems in the last five years?
- Has the company been involved in, or is aware of, any disputes over any domain names under their control in the last five years?
- If yes to any of the above, attach details.
Changes
Over time, if any of this changes you need to inform your insurer so your policy is modified accordingly.
HOW MUCH DOES CYBERSECURITY INSURANCE COST?

The type, size, and the business model you have as well as the way you utilize technology are going to reflect the type of cybersecurity coverage you need and are able to be approved for. Insurance companies premiums are based on statistics and the insurance companies are aware of the stats or risk of people who follow best practices and the stats or risk of companies that don’t. Ensuring your business has strong security controls is your best defense both against any attacks and to secure cyber insurance.

WILL WORK WITH YOU TO BECOME COMPLIANT AND INSURED.
GIVE US A CALL TODAY
