
Located all over the world and largest threat hunting service of its kind with full scale incident response
Our multiple teams & flexible service levels are designed to be Compatible with your environment needs
Each business and environment is different with unique needs. You choose what service level works best for you. We can use our tools, your tools or a combinations of the both to customize a solution to fit your businesses needs.
Reasons companies retain our cybersecurity teams:

option one – We Supply all security Tools
The Cybersecurity Team will use a consolidation of tools and data that provides extended visibility, analysis, and response across networks and clouds in addition to apps and endpoints.
These tools push critical telemetry to the Security Operations Centre (SOC) improving threat detection and visibility for highly-trained threat hunters, engineers, and ethical hackers for investigating and responding to threats.
Cybersecurity Compliance Services supplies you with all the tools needed for the Cybersecurity Team to manage your environment. This option is the most cost effective, most often selected, best integrated and it is already part of our Endpoint Protection Suite.
option two – using your security monitoring and alerting systems
You have financially invested in your own software and hardware and would like Cybersecurity Compliance Services to provide you a team to monitor and respond to threats on your behalf. The Cybersecurity Team will absorb all available metrics from your existing toolsets into our Security Operations Center.
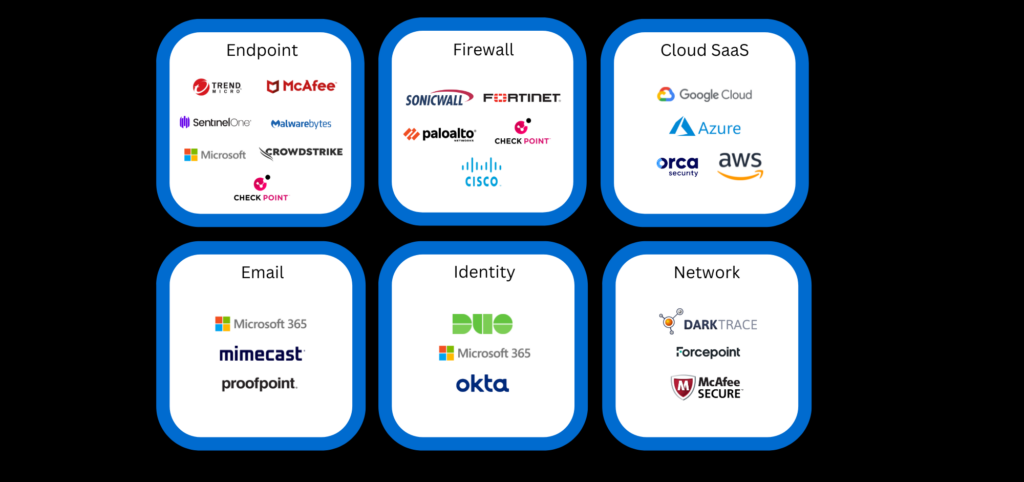
Best suited for a company that uses the below tools.
OUR SECURITY TEAM CAN ABSORB YOUR METRICS FROM THE FOLLOWING:

option three – hybrid combination of your exsiting tools and our tools
Combining both “Option One” and “Option Two”. Your tools and our tools will be utilized by the Cybersecurity Team to manage your environment.
Best suited for a company that wants to use our tools and have us manage the above tools in our Security Operations Center.
option four – Vulnerability Management Team
The Vulnerability Management Team works on your behalf to secure your endpoints to your specific compliance standards, reducing attack surface while continually scanning for OS and application vulnerabilities.
Best suited for a company that is working towards a compliance standard and needs a vulnerability management program in place.
